…so meanwhile you can read about SQL injection and prepared statements. ![]()
Also, to ensure the requests are really coming from TTN:
-
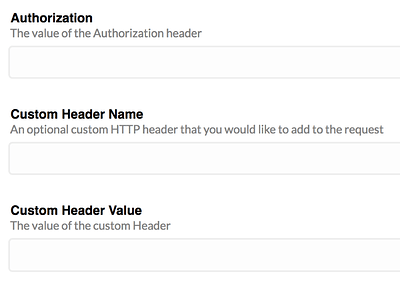
Set a value for the integration’s
AuthorizationHTTP header (beware that some servers might only support the officialAuthorization: <type> <credentials>syntax, and might even ignore invalid values when using Basic Access Authentication or Digest Access Authentication; see references in my other answer below). Or add a custom header and a value†, and validate that in your code: -
Or: add some authentication to the URL (something like
ttnpost.php?myauth=my-super-secret) -
Or: check the key in
downlink_urlagainst what you know is correct -
Or: or use a random URL (like
my-super-secret-h7dnt01kqq9.php)
† Added to this answer September 2017; the Authorization header and custom header were added to the integration somewhere after its initial release, and after the initial version of this answer, as posted February 2017.