My network knowledge is basic but I think I see traffic coming in on port 1700 upd and I also see outgoing traffic on port 1700 upd. See also attached print screen of the sniffer
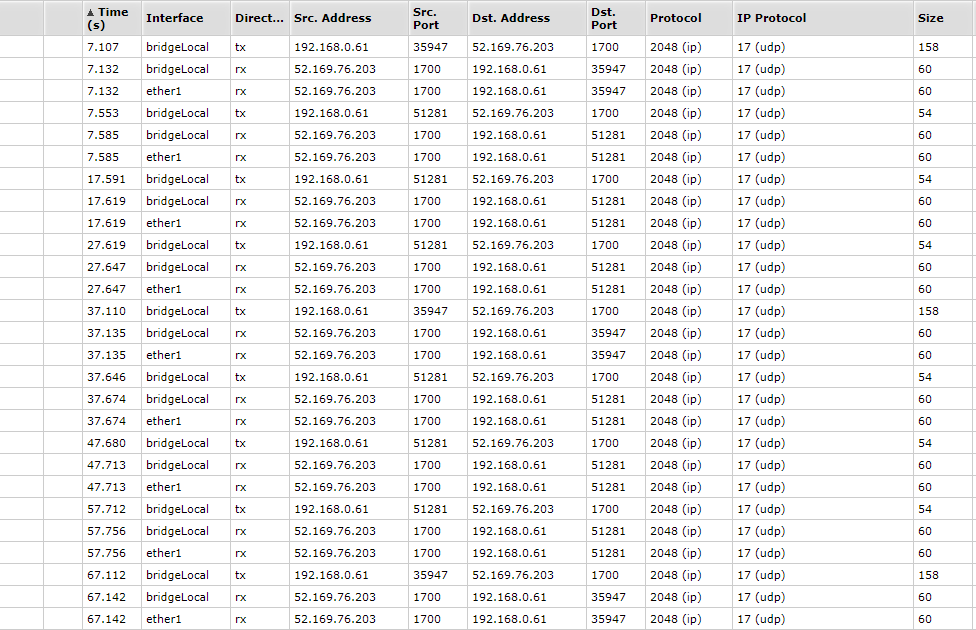
My network knowledge is basic but I think I see traffic coming in on port 1700 upd and I also see outgoing traffic on port 1700 upd. See also attached print screen of the sniffer
