Got the E5 working in short order, then once again work and the likes got in the way.
Back to it tonight and have again sent the test outlined in this page…
Raspberry Pi Pico with LoRaWAN and The Things Network - Makerverse LoRa-E5 Module - Transmit Weather Data into IoT - Tutorial Australia (core-electronics.com.au)
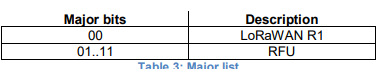
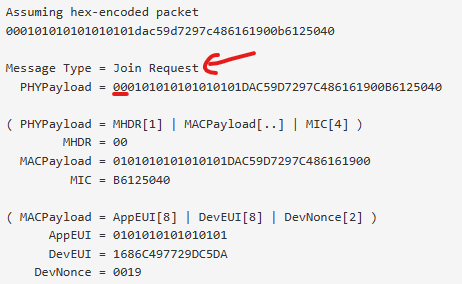
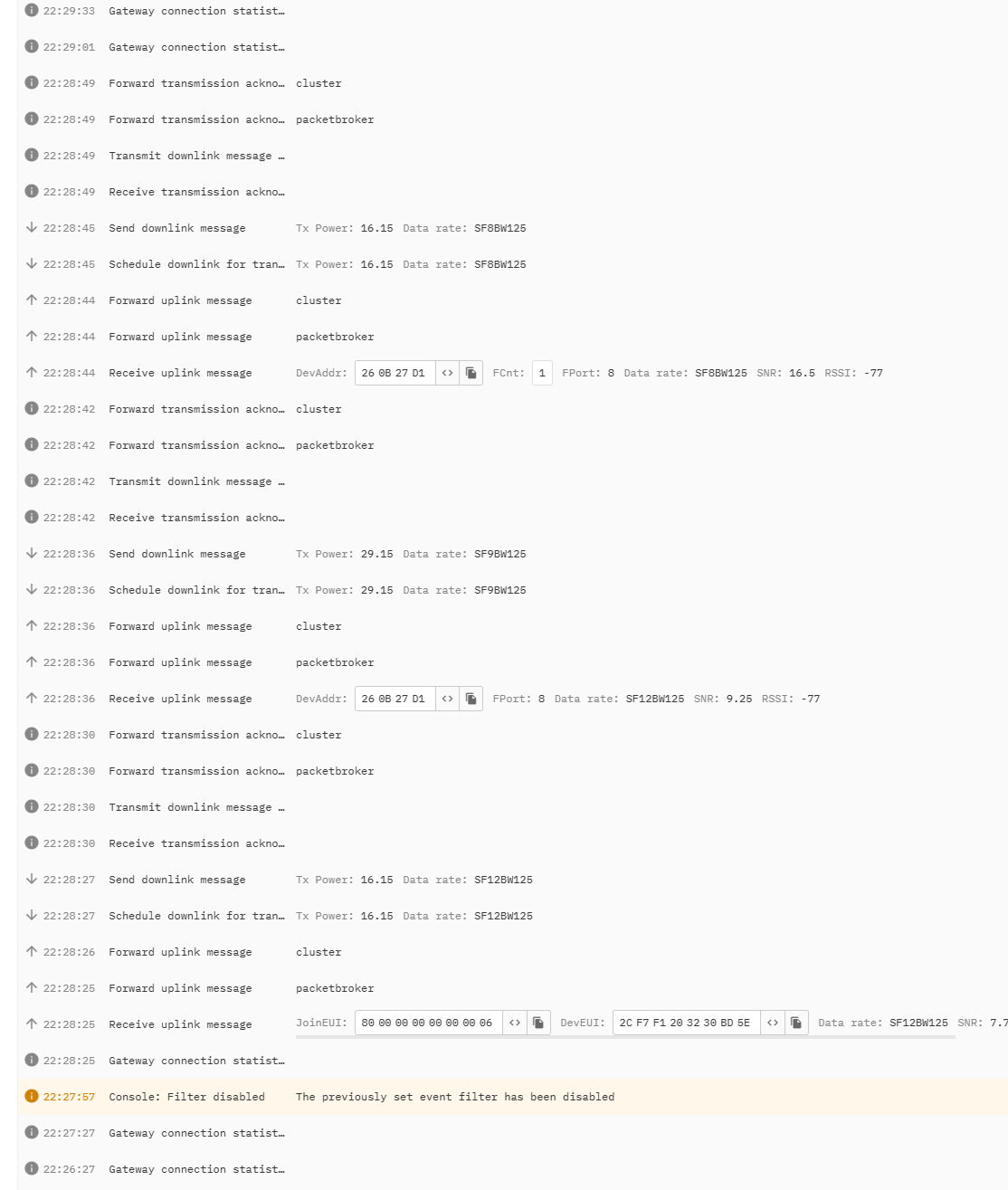
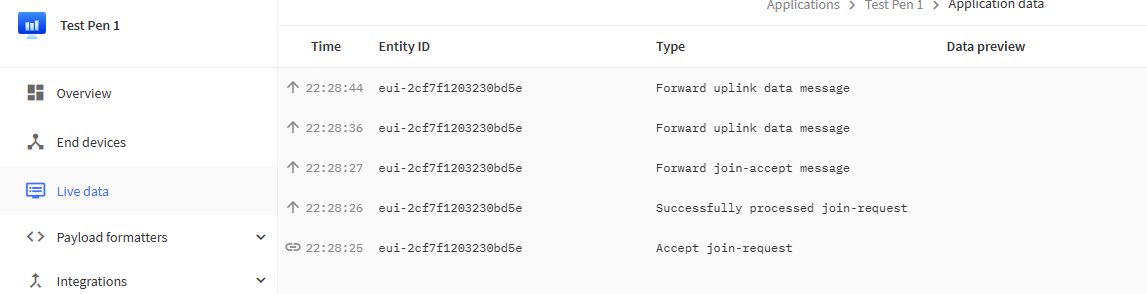
Which should contain 2 payloads (if you search for “Payload 1” you find it). Looking in TTN Gateway Console I can see 3 uplinks, each followed by a downlink - which makes sense. What I can’t see in any of the uplinks is a payload that in anyway matches the 2 payloads I’m meant to be seeing. Sadly the screen shots aren’t clear, but it looks like they are actually looking under the application, but I can’t see them there either.
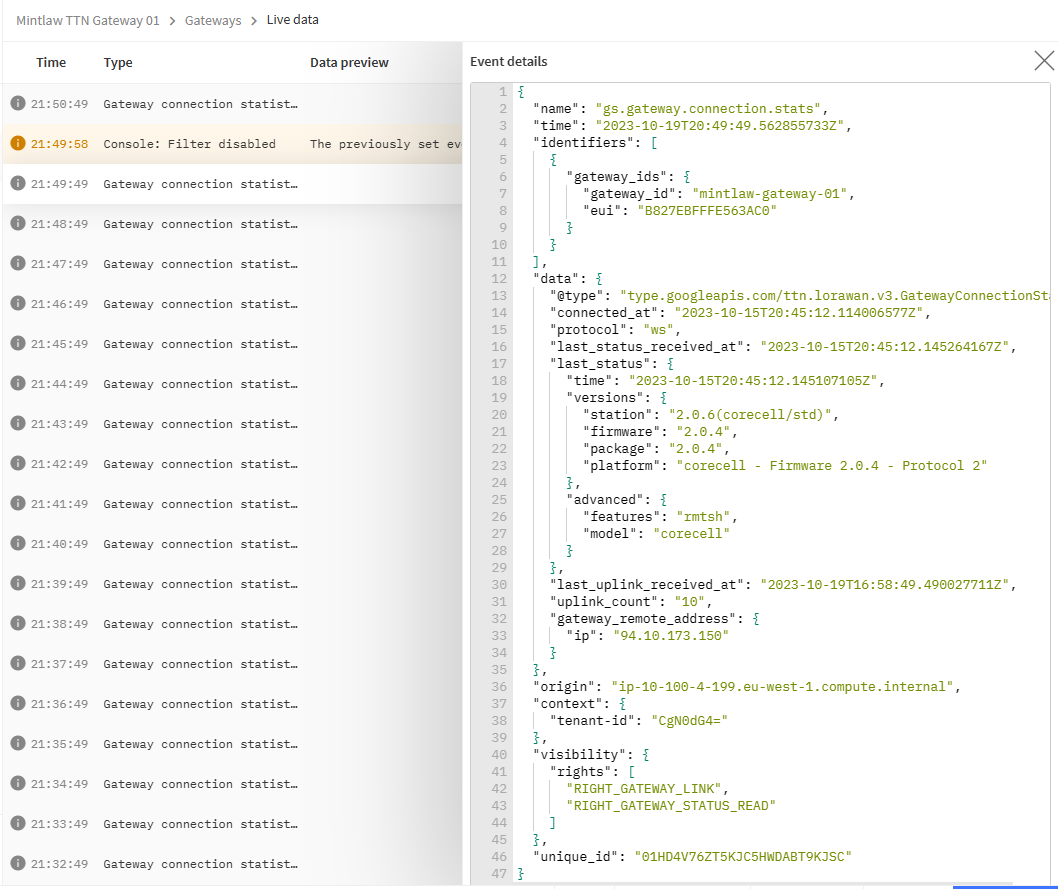
The following is the Gateway live data…
I’m assuming I should find the payload in the detail panel when clicking on the 3 “receive uplink message” lines, but I don’t - unless it has become encoded into the raw in what looks like Base64
1st
{
"name": "gs.up.receive",
"time": "2023-11-10T22:28:25.971716942Z",
"identifiers": [
{
"gateway_ids": {
"gateway_id": "mintlaw-gateway-01",
"eui": "B827EBFFFE563AC0"
}
}
],
"data": {
"@type": "type.googleapis.com/ttn.lorawan.v3.GatewayUplinkMessage",
"message": {
"raw_payload": "AAYAAAAAAACAXr0wMiDx9yyQu8dpgJU=",
"payload": {
"m_hdr": {},
"mic": "x2mAlQ==",
"join_request_payload": {
"join_eui": "8000000000000006",
"dev_eui": "2CF7F1203230BD5E",
"dev_nonce": "BB90"
}
},
"settings": {
"data_rate": {
"lora": {
"bandwidth": 125000,
"spreading_factor": 12,
"coding_rate": "4/5"
}
},
"frequency": "868500000",
"timestamp": 3497045146,
"time": "2023-11-10T22:28:25.960534095Z"
},
"rx_metadata": [
{
"gateway_ids": {
"gateway_id": "mintlaw-gateway-01",
"eui": "B827EBFFFE563AC0"
},
"time": "2023-11-10T22:28:25.960534095Z",
"timestamp": 3497045146,
"rssi": -78,
"channel_rssi": -78,
"snr": 7.75,
"location": {
"latitude": 57.52503521045234,
"longitude": -2.004565000534058,
"source": "SOURCE_REGISTRY"
},
"uplink_token": "CiAKHgoSbWludGxhdy1nYXRld2F5LTAxEgi4J+v//lY6wBCa2cKDDRoMCInduqoGEMW8os8DIJDziMHj/CI=",
"received_at": "2023-11-10T22:28:25.953815107Z"
}
],
"received_at": "2023-11-10T22:28:25.971546181Z",
"correlation_ids": [
"gs:uplink:01HEXNKJQKE4KHB28SBYF08GH9"
]
},
"band_id": "EU_863_870"
},
"correlation_ids": [
"gs:uplink:01HEXNKJQKE4KHB28SBYF08GH9"
],
"origin": "ip-10-100-7-161.eu-west-1.compute.internal",
"context": {
"tenant-id": "CgN0dG4="
},
"visibility": {
"rights": [
"RIGHT_GATEWAY_TRAFFIC_READ"
]
},
"unique_id": "01HEXNKJQKAM2X6CAXW7JDP3DW"
}
2nd
{
"name": "gs.up.receive",
"time": "2023-11-10T22:28:36.468274375Z",
"identifiers": [
{
"gateway_ids": {
"gateway_id": "mintlaw-gateway-01",
"eui": "B827EBFFFE563AC0"
}
}
],
"data": {
"@type": "type.googleapis.com/ttn.lorawan.v3.GatewayUplinkMessage",
"message": {
"raw_payload": "QNEnCyaAAAAI4gNpEF4GaFcC6O1sFz7ALg==",
"payload": {
"m_hdr": {
"m_type": "UNCONFIRMED_UP"
},
"mic": "Fz7ALg==",
"mac_payload": {
"f_hdr": {
"dev_addr": "260B27D1",
"f_ctrl": {
"adr": true
}
},
"f_port": 8,
"frm_payload": "4gNpEF4GaFcC6O1s"
}
},
"settings": {
"data_rate": {
"lora": {
"bandwidth": 125000,
"spreading_factor": 12,
"coding_rate": "4/5"
}
},
"frequency": "868500000",
"timestamp": 3507541181,
"time": "2023-11-10T22:28:36.457109928Z"
},
"rx_metadata": [
{
"gateway_ids": {
"gateway_id": "mintlaw-gateway-01",
"eui": "B827EBFFFE563AC0"
},
"time": "2023-11-10T22:28:36.457109928Z",
"timestamp": 3507541181,
"rssi": -77,
"channel_rssi": -77,
"snr": 9.25,
"location": {
"latitude": 57.52503521045234,
"longitude": -2.004565000534058,
"source": "SOURCE_REGISTRY"
},
"uplink_token": "CiAKHgoSbWludGxhdy1nYXRld2F5LTAxEgi4J+v//lY6wBC9qcOIDRoMCJTduqoGEJ2um98BIMiE/M2K/SI=",
"received_at": "2023-11-10T22:28:36.422155853Z"
}
],
"received_at": "2023-11-10T22:28:36.468113181Z",
"correlation_ids": [
"gs:uplink:01HEXNKWZMNV3QNVS0R2G8KY5Z"
]
},
"band_id": "EU_863_870"
},
"correlation_ids": [
"gs:uplink:01HEXNKWZMNV3QNVS0R2G8KY5Z"
],
"origin": "ip-10-100-7-161.eu-west-1.compute.internal",
"context": {
"tenant-id": "CgN0dG4="
},
"visibility": {
"rights": [
"RIGHT_GATEWAY_TRAFFIC_READ"
]
},
"unique_id": "01HEXNKWZM9HCHYMGS1H5D4S3B"
}
3rd
{
"name": "gs.up.receive",
"time": "2023-11-10T22:28:44.594079793Z",
"identifiers": [
{
"gateway_ids": {
"gateway_id": "mintlaw-gateway-01",
"eui": "B827EBFFFE563AC0"
}
}
],
"data": {
"@type": "type.googleapis.com/ttn.lorawan.v3.GatewayUplinkMessage",
"message": {
"raw_payload": "QNEnCyaFAQADBwb/CgiM1Sr8v1svvT0l0DRatRp4KTNCVQ==",
"payload": {
"m_hdr": {
"m_type": "UNCONFIRMED_UP"
},
"mic": "KTNCVQ==",
"mac_payload": {
"f_hdr": {
"dev_addr": "260B27D1",
"f_ctrl": {
"adr": true
},
"f_cnt": 1,
"f_opts": "AwcG/wo="
},
"f_port": 8,
"frm_payload": "jNUq/L9bL709JdA0WrUaeA=="
}
},
"settings": {
"data_rate": {
"lora": {
"bandwidth": 125000,
"spreading_factor": 8,
"coding_rate": "4/5"
}
},
"frequency": "867300000",
"timestamp": 3515690416,
"time": "2023-11-10T22:28:44.582701921Z"
},
"rx_metadata": [
{
"gateway_ids": {
"gateway_id": "mintlaw-gateway-01",
"eui": "B827EBFFFE563AC0"
},
"time": "2023-11-10T22:28:44.582701921Z",
"timestamp": 3515690416,
"rssi": -77,
"channel_rssi": -77,
"snr": 16.5,
"location": {
"latitude": 57.52503521045234,
"longitude": -2.004565000534058,
"source": "SOURCE_REGISTRY"
},
"uplink_token": "CiAKHgoSbWludGxhdy1nYXRld2F5LTAxEgi4J+v//lY6wBCw27SMDRoMCJzduqoGEN6mmpsCIIDv6fuo/SI=",
"received_at": "2023-11-10T22:28:44.561212519Z"
}
],
"received_at": "2023-11-10T22:28:44.593924958Z",
"correlation_ids": [
"gs:uplink:01HEXNM4XJ0DNEEJYRB3RVP0AT"
]
},
"band_id": "EU_863_870"
},
"correlation_ids": [
"gs:uplink:01HEXNM4XJ0DNEEJYRB3RVP0AT"
],
"origin": "ip-10-100-7-161.eu-west-1.compute.internal",
"context": {
"tenant-id": "CgN0dG4="
},
"visibility": {
"rights": [
"RIGHT_GATEWAY_TRAFFIC_READ"
]
},
"unique_id": "01HEXNM4XJCMW6JJB6PJPHQH6R"
}