Hello,
I would like to configure The Things Stack behind a reverse proxy for the web console (to prevent web attack, the console is available on internet).
More specifically, our reverse proxy is an apache stack with mod_proxy and mod_security to filter inbound request (L7 firewall).
Moreover, I would like that the other ports (used for communication between the gateways and the application) don’t pass through the proxy.
I’m unable to configure FQDN correctly in my ‘ttn-lw-stack-docker.yml’ file.
Whare are parameters to configure with the proxy FQDN and other with server FQDN ?
Is it possible to have an example config file for my environment ?
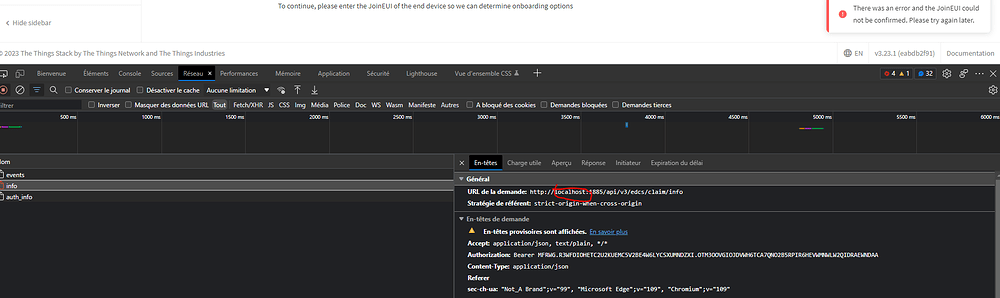
I tried to replace only FQDN in web URL (https://the-things-stack.umons.ac.be/) with the proxy URL and keep server URL for other parameters but it doesn’t work !
Sorry if the post already exists !
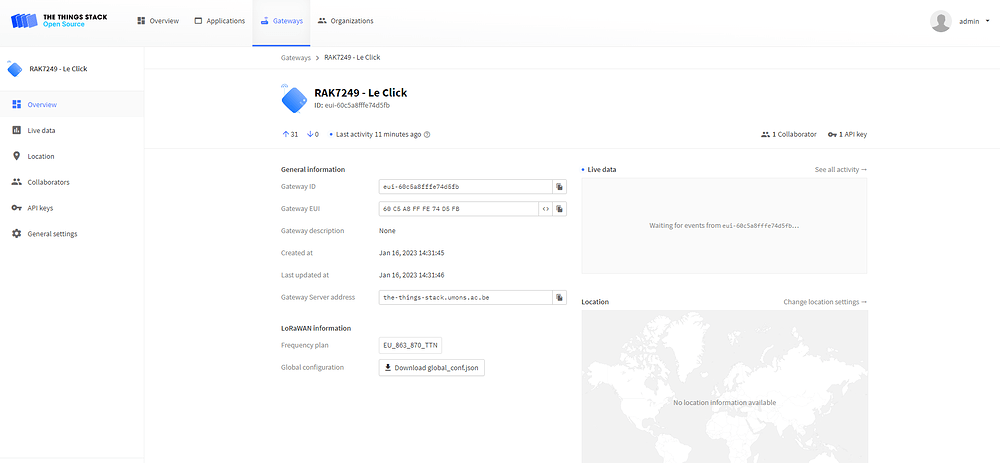
Here is my config :
# Identity Server configuration
# Email configuration for "the-things-stack.umons.ac.be"
is:
email:
sender-name: 'The Things Stack'
sender-address: 'the-things-stack@apps.umons.ac.be'
network:
name: 'The Things Stack'
console-url: 'https://the-things-stack.umons.ac.be/console'
identity-server-url: 'https://the-things-stack.umons.ac.be/oauth'
provider: smtp
smtp:
address: 'xxx'
# username: '' # enter SMTP server username
# password: '' # enter SMTP server password
# Web UI configuration for "the-things-stack.umons.ac.be":
oauth:
ui:
canonical-url: 'https://the-things-stack.umons.ac.be/oauth'
is:
base-url: 'https://the-things-stack.umons.ac.be/api/v3'
# HTTP server configuration
http:
cookie:
block-key: 'xxx' # generate 32 bytes (openssl rand -hex 32)
hash-key: 'xxx' # generate 64 bytes (openssl rand -hex 64)
metrics:
password: 'xxx' # choose a password
pprof:
password: 'xxx' # choose a password
# If using custom certificates:
tls:
source: file
root-ca: /run/secrets/ca.pem
certificate: /run/secrets/cert.pem
key: /run/secrets/key.pem
# Let's encrypt for "the-things-stack.umons.ac.be"
#tls:
# source: 'acme'
# acme:
# dir: '/var/lib/acme'
# email: 'you@the-things-stack.umons.ac.be'
# hosts: ['the-things-stack.umons.ac.be']
# default-host: 'the-things-stack.umons.ac.be'
# If Gateway Server enabled, defaults for "the-things-stack.umons.ac.be":
gs:
mqtt:
public-address: 'the-things-stack.umons.ac.be:1882'
public-tls-address: 'the-things-stack.umons.ac.be:8882'
mqtt-v2:
public-address: 'the-things-stack.umons.ac.be:1881'
public-tls-address: 'the-things-stack.umons.ac.be:8881'
# If Gateway Configuration Server enabled, defaults for "the-things-stack.umons.ac.be":
gcs:
basic-station:
default:
lns-uri: 'wss://the-things-stack.umons.ac.be:8887'
the-things-gateway:
default:
mqtt-server: 'mqtts://the-things-stack.umons.ac.be:8881'
# Web UI configuration for "the-things-stack.umons.ac.be":
console:
ui:
canonical-url: 'https://the-things-stack.umons.ac.be/console'
is:
base-url: 'https://the-things-stack.umons.ac.be/api/v3'
gs:
base-url: 'https://the-things-stack.umons.ac.be/api/v3'
gcs:
base-url: 'https://the-things-stack.umons.ac.be/api/v3'
ns:
base-url: 'https://the-things-stack.umons.ac.be/api/v3'
as:
base-url: 'https://the-things-stack.umons.ac.be/api/v3'
js:
base-url: 'https://the-things-stack.umons.ac.be/api/v3'
qrg:
base-url: 'https://the-things-stack.umons.ac.be/api/v3'
edtc:
base-url: 'https://the-things-stack.umons.ac.be/api/v3'
oauth:
authorize-url: 'https://the-things-stack.umons.ac.be/oauth/authorize'
token-url: 'https://the-things-stack.umons.ac.be/oauth/token'
logout-url: 'https://the-things-stack.umons.ac.be/oauth/logout'
client-id: 'console'
client-secret: 'xxx' # choose or generate a secret
# If Application Server enabled, defaults for "the-things-stack.umons.ac.be":
as:
mqtt:
public-address: 'the-things-stack.umons.ac.be:1883'
public-tls-address: 'the-things-stack.umons.ac.be:8883'
webhooks:
downlink:
public-address: 'the-things-stack.umons.ac.be:1885/api/v3'
# If Device Claiming Server enabled, defaults for "the-things-stack.umons.ac.be":
dcs:
oauth:
authorize-url: 'https://the-things-stack.umons.ac.be/oauth/authorize'
token-url: 'https://the-things-stack.umons.ac.be/oauth/token'
logout-url: 'https://the-things-stack.umons.ac.be/oauth/logout'
client-id: 'device-claiming'
client-secret: 'xxx' # choose or generate a secret
ui:
canonical-url: 'https://the-things-stack.umons.ac.be/claim'
as:
base-url: 'https://the-things-stack.umons.ac.be/api/v3'
dcs:
base-url: 'https://the-things-stack.umons.ac.be/api/v3'
is:
base-url: 'https://the-things-stack.umons.ac.be/api/v3'
ns:
base-url: 'https://the-things-stack.umons.ac.be/api/v3'
grpc:
trusted-proxies: 'xxx,xxxx,xxx,xxx'
Thank you for your help !
Regards,
Maxence Danvain