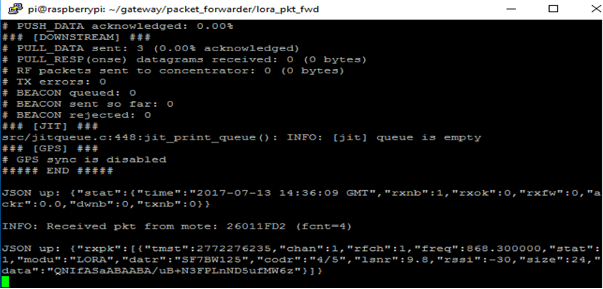
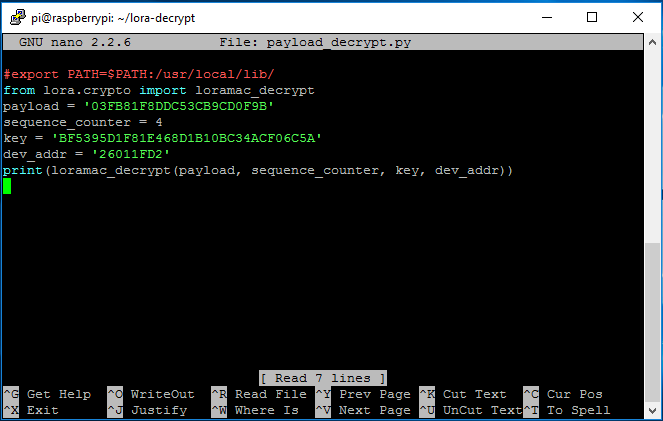
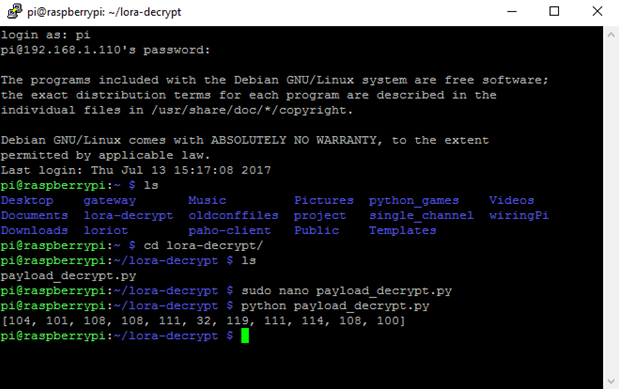
Hello,
I have found this code able to decrypt a LoRaWAN packet. Tha problem is that I could’nt use it 
it is basically unsing this function to decrypt LoRaWAN packet:
byte fport= (byte) 0x01;//Byte.valueOf("1");
byte dirValue = (byte) 0x00;//Byte.valueOf("0");
byte[] devAddr = {0x08,0x00,0x00,0x00};//hexStringToByteArray("08000000");
short fCnt = 200;
public byte[] getClearPayLoad(byte[] payload, byte[] _nwkSKey, byte[] _appSKey) throws NoSuchAlgorithmException, NoSuchPaddingException, InvalidKeyException, IllegalBlockSizeException, BadPaddingException, MalformedPacketException {
byte[] key;
if (fport == 0) {
if (_nwkSKey == null) {
throw new IllegalArgumentException("Missing nwkSKey");
}
if (_nwkSKey.length != 16) {
throw new IllegalArgumentException("Invalid nwkSKey");
}
key = _nwkSKey;
} else {
if (_appSKey == null) {
throw new IllegalArgumentException("Missing appSKey");
}
if (_appSKey.length != 16) {
throw new IllegalArgumentException("Invalid appSKey");
}
key = _appSKey;
}
int k = (int) Math.ceil(payload.length / 16.0);
System.out.println("payload length: "+payload.length);
System.out.println("k is: "+ k);
ByteBuffer a = ByteBuffer.allocate(16 * k);
a.order(ByteOrder.LITTLE_ENDIAN);
for (int i = 1; i <= k; i++) {
a.put((byte) 0x01);
a.put(new byte[]{0x00, 0x00, 0x00, 0x00});
a.put(dirValue);
a.put(devAddr);
a.putInt(fCnt);
a.put((byte) 0x00);
a.put((byte) i);
}
Key aesKey = new SecretKeySpec(key, "AES");
Cipher cipher = Cipher.getInstance("AES");
cipher.init(Cipher.ENCRYPT_MODE, aesKey);
byte[] s = cipher.doFinal(a.array());
byte[] paddedPayload = new byte[16 * k];
System.arraycopy(payload, 0, paddedPayload, 0, payload.length);
byte[] plainPayload = new byte[payload.length];
for (int i = 0; i < payload.length; i++) {
plainPayload[i] = (byte) (s[i] ^ paddedPayload[i]);
}
return plainPayload;
}
So what I did is the following:
byte[] appSKey = new byte[] { 0x2B, 0x7E, 0x15, 0x16, 0x28, (byte) 0xAE, (byte) 0xD2, (byte) 0xA6,(byte) 0xAB, (byte) 0xF7, 0x15, (byte) 0x88, 0x09,(byte) 0xCF, 0x4F, 0x3C};
byte[] nwkSKey = new byte[] { 0x2B, 0x7E, 0x15, 0x16, 0x28, (byte) 0xAE, (byte) 0xD2, (byte) 0xA6, (byte) 0xAB,(byte) 0xF7, 0x15, (byte) 0x88, 0x09,(byte) 0xCF, 0x4F, 0x3C};
byte[] payload = new byte[] {0x40,0x08,0x00,0x00,0x00,0x00,0x02,0x00,0x01,0x6B,(byte) 0xD9,0x4F,0x33,(byte) 0xB4,(byte) 0xC9,(byte) 0xB7,0x4D,(byte) 0xA8,0x26,0x3E,(byte) 0xD0,(byte) 0xAC,0x09, (byte)0xE5, (byte)0xA9,(byte) 0xB2, 0x6D, 0x01, (byte)0x89, 0x15, 0x47,(byte) 0xEA, 0x2F, (byte)0x89, 0x2F, 0x06};
MyLoRaPayloadDecrypter loRaPayloadDecrypter =new MyLoRaPayloadDecrypter();
try {
byte[] decrypted = loRaPayloadDecrypter.getClearPayLoad(payload, nwkSKey, appSKey);
System.out.println(new String(decrypted));
} catch (InvalidKeyException | NoSuchAlgorithmException | NoSuchPaddingException | IllegalBlockSizeException
| BadPaddingException | MalformedPacketException e) {
// TODO Auto-generated catch block
e.printStackTrace();
}
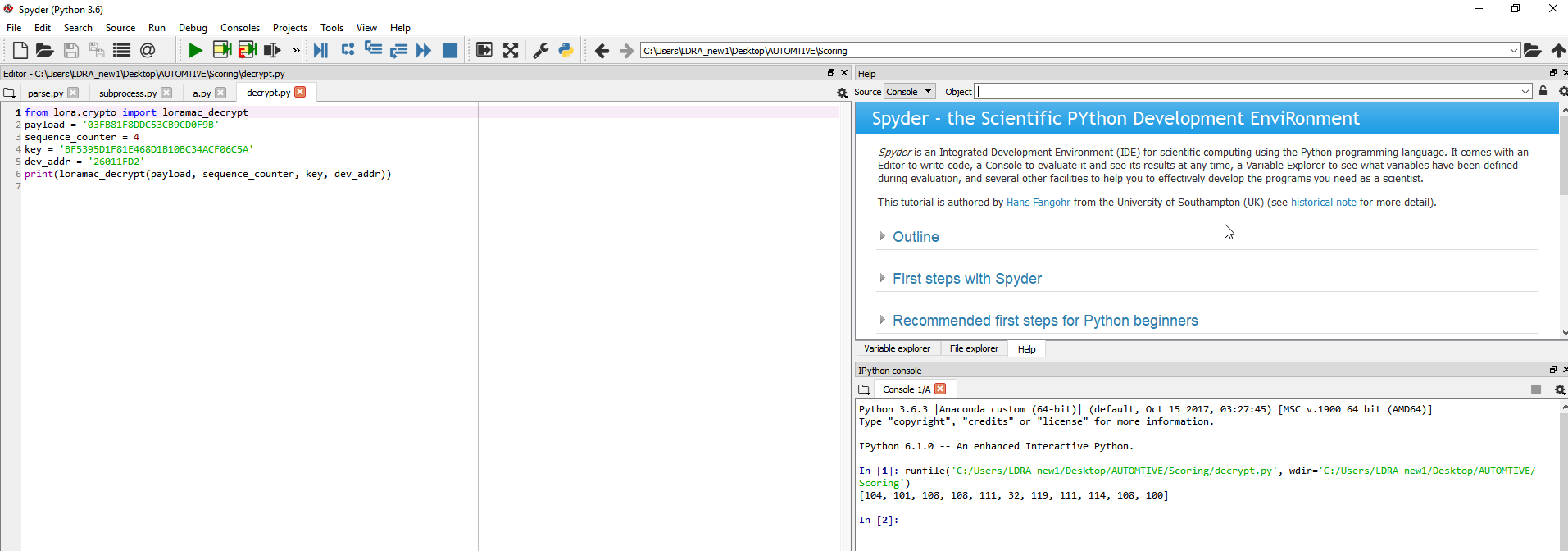
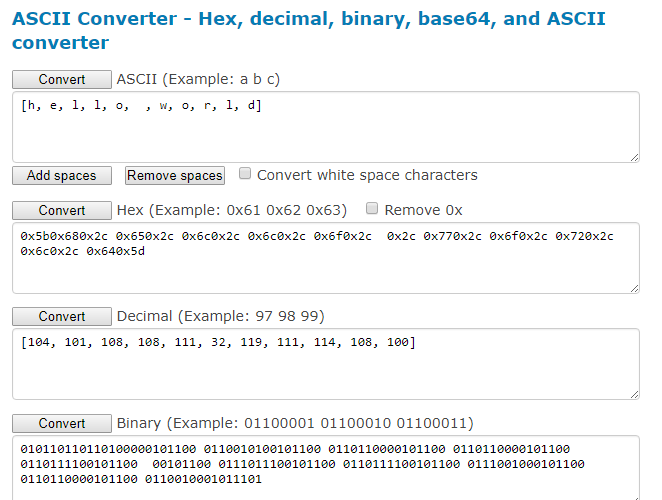
But I am getting dummy values…
Any idea how to decrypt LoRaWAN packet in Java?
thanks!